Following on the heels of Windows 8 and the problems associated with the acceptance of the Metro interface, Microsoft is preparing for the release of Windows 10 in the next few months.
Read more
Friday, October 3, 2014
Tuesday, May 6, 2014
Windows XP: Microsoft can't wash its hands of the security problem so easily
Late last week, Microsoft published an unexpected security update for a flaw in its Internet Explorer browser. Even more unexpected, the patch also covered Windows XP, which Microsoft officially stopped supporting back in early April.
Microsoft explained the change of heart by saying it had provided the security update "based on the proximity to the end of support for Windows XP".
Richmond Computer believes this update was forced out with pressure from the Department of Homeland security who advised the public not to use Microsoft Internet Explorer because of this security flaw.
Symantec calls antivirus 'doomed' as security giants fight for survival
Antivirus products are catching less than half of all cyberattacks and is no longer a money maker for companies that produce and support endpoint security products. While Microsoft continues to operate it's Security Essentials platform, it also has less than stellar results when it comes to blocking attacks.
Richmond Computer provides an antivirus solution for as low as $2/month. While our platform does not guarantee to stop all viruses, we do include the ability to catch viruses and deploy countermeasures in real time.
Monday, May 5, 2014
Bring the start menu back to Windows 8
Tired on the Metro screen on Windows 8? Now there's a solution:
http://candysoft.com/istartmenu/
Monday, March 10, 2014
The internet turns 25
In March 1989 the internet made its debut as an invention by Tim Berners-Lee and remains the fastest growing means of communication. While other forms of communication have evolved and modernized over time (mail, telegraph, telephone, etc), none have seen the endless amount of innovation that the internet has produced in such a short period of time.
The use of computers has vastly changed since 1989, which was a time when most computers were manufactured by IBM (who developed the IBM PC Jr.), had monochrome screens, and were usually stand-alone systems and not part of any network.
The early days of the internet not only used primitive machines, but also very slow means of communication by today's standards. When we mention the internet, most computer users think of the World Wide Web (www.yourfavoritewebsite.com), which the internet is not. The Internet is a global system of interconnected networks that use a standard protocol (TCP/IP) for communication. The internet is literally the connection of millions of private and public computer networks that consist of schools, businesses and government agencies, linked by a broad array of electronic, wireless, and optical networking technologies.
Today's internet use in simple terms consists of social uses, financial transactions, research, and sharing of data. While use of the internet did not go mainstream until 1995 with the release of Microsoft Windows 95 (the days when we all used dial-up modems), its use has rapidly developed and evolved, and has reshaped how we live our lives. This evolution will continue, and I'm sure future generations will look back on today's internet uses as primitive.
Thursday, February 6, 2014
Wednesday, February 5, 2014
LegalTech NYC 2014
Today we attended the bi-annual LegalTech conference and expo in New York City. This year, LegalTech was held at the Midtown Manhattan Hilton at 54th & 6th Avenues.
LegalTech gave Richmond Computer the opportunity to discuss the SMS Witness smartphone text message transcription service with some of the top E-discovery firms in the nation for the purpose of adding new enhancements to our existing service. Future services will include conversion of voicemails to printable transcripts and Geo-coding of data and events on mobile devices.
LegalTech is the most important legal technology event of the year. Legal Technology is ever changing and LegalTech offers law firms and legal departments the ability to stay on top of this evolving industry to improve their law practice management.LegalTech features presentations and vendor displays from the top names in the industry including Concordance, Symantec, KPMG, LexisNexis, Xerox, Ernst & Young, Scarab Consulting, Nuance Communications, and many others.
LegalTech gave Richmond Computer the opportunity to discuss the SMS Witness smartphone text message transcription service with some of the top E-discovery firms in the nation for the purpose of adding new enhancements to our existing service. Future services will include conversion of voicemails to printable transcripts and Geo-coding of data and events on mobile devices.
Friday, January 31, 2014
Windows 8 Metro interface takes a back seat in latest service pack
Leaks from Microsoft's Redmond, Washington headquarters have revealed that an upcoming product release in March will turn off the Metro "start screen" by default, sending users to the traditional desktop screen when Windows 8.1 systems boot up.
Since the release of Windows 8, end users, resellers and industry consultants have lambasted Microsoft for forcing such drastic changes into the desktop environment, especially for business applications. Microsoft's initial strategic plan was to create a universal interface applicable to all electronic devices carrying their operating system: smartphones, tablets, laptops, desktops and servers. However, most desktop users have found the Metro interface to be clumsy and difficult to use compared to the traditional desktop with start button.
Microsoft's new tiled "Metro" interface may be great for Windows based smartphones (if anyone buys them), or the Surface, but it leaves much to be desired in the office or home desktop. Most users complain it has become much harder to find the apps they need, setting up the Metro tiles, and shutting down the machine (it now takes 4 clicks instead of 2). Metro may be great because it tells you the temperature in Sydney, Australia, but if you're looking for Microsoft Word, well, you have to type it in by hand.
Without clear thought, Microsoft has eliminated the one feature that made their system stand out from all the rest: the beloved Start Button. The steering wheel we grew up with since Windows 95 is now gone, replaced by a preset screen of tiles. Microsoft could have done a lot to make this transition smoother, such as by putting boot-to-touch only on touch-based PCs and then having a toggle button to go from the touch interface to the traditional Windows interface. Or work with the track-pad vendors to map to touch while still keeping the Start Button in place as an option.
This strategic blunder has kept millions of people from migrating to the world of Windows 8. Those that can are buying systems with Windows 7, or simply holding on to existing systems (Microsoft is doing all it can to rip Windows XP machines from your hands---Support ends April 8, 2014!). Microsoft’s blunder has cost it and its partners dearly, and may continue until Windows 9 is released in the spring of 2015.
Read more: Microsoft’s Strategic Blunder with Windows 8 | TIME.com http://techland.time.com/2013/05/06/microsofts-strategic-blunder-with-windows-8/#ixzz2s0X1dSp6
Since the release of Windows 8, end users, resellers and industry consultants have lambasted Microsoft for forcing such drastic changes into the desktop environment, especially for business applications. Microsoft's initial strategic plan was to create a universal interface applicable to all electronic devices carrying their operating system: smartphones, tablets, laptops, desktops and servers. However, most desktop users have found the Metro interface to be clumsy and difficult to use compared to the traditional desktop with start button.
Microsoft's new tiled "Metro" interface may be great for Windows based smartphones (if anyone buys them), or the Surface, but it leaves much to be desired in the office or home desktop. Most users complain it has become much harder to find the apps they need, setting up the Metro tiles, and shutting down the machine (it now takes 4 clicks instead of 2). Metro may be great because it tells you the temperature in Sydney, Australia, but if you're looking for Microsoft Word, well, you have to type it in by hand.
Without clear thought, Microsoft has eliminated the one feature that made their system stand out from all the rest: the beloved Start Button. The steering wheel we grew up with since Windows 95 is now gone, replaced by a preset screen of tiles. Microsoft could have done a lot to make this transition smoother, such as by putting boot-to-touch only on touch-based PCs and then having a toggle button to go from the touch interface to the traditional Windows interface. Or work with the track-pad vendors to map to touch while still keeping the Start Button in place as an option.
 |
| Windows 95 desktop |
This strategic blunder has kept millions of people from migrating to the world of Windows 8. Those that can are buying systems with Windows 7, or simply holding on to existing systems (Microsoft is doing all it can to rip Windows XP machines from your hands---Support ends April 8, 2014!). Microsoft’s blunder has cost it and its partners dearly, and may continue until Windows 9 is released in the spring of 2015.
Read more: Microsoft’s Strategic Blunder with Windows 8 | TIME.com http://techland.time.com/2013/05/06/microsofts-strategic-blunder-with-windows-8/#ixzz2s0X1dSp6
Thursday, January 30, 2014
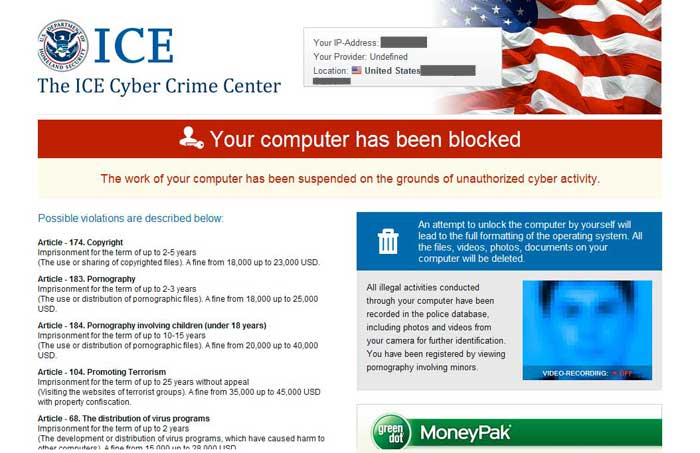
Beware Computer Locking ICE Virus
ICE virus (also called as The Cyber Crimes Center virus) is a dangerous ransomware, which must be ignored and eliminated from each of its affected computers. You can distinguish this virus from a huge notification, which lists various crimes and requires to pay the fine of 400 dollars or other reasonable amount of money. Typically, ICE virus mentions the distribution of pornographic files, the use of copyrighted content and similar crimes. While it may seem that this is an official notification from a governmental organization, it's just a typical scam that must be avoided. In order to trick its target PC users, ICE virus starts its activity by blocking the whole system down while there is no such governmental organization that blocks PCs to collect their fines. The real owner of this cyber threat is a huge group of cyber criminals that use different versions of such viruses for trying to rip people off. You must remove ICE The Cyber Crimes Center virus without any delay.
ICE Cyber Crimes Center virus, just like Your computer has been blocked virus, is distributed via trojan horse. Mostly, users download this infection together with unofficial programs and their updates that are spread on illegal websites. Besides, misleading emails that also pretend to be sent by this official organization can easily let this trojan inside. Once it gets there, this dangerous threat blocks the whole system and downloads those files that are needed for ICE virus. SO, it can be said that ransomware takes its target PC a hostage and then replaces desktop's screen with a message that claims something like that:
As a preventative measure, we suggest having an IMAGE of your system made, using one of Richmond Computer's imaging tools.The image is made by our software, and would be stored on a series of DVDs or external USB drive.
For a consultation on the state of your system's backup, please contact Richmond Computer at (215)634-2997 or sales@richmondcomputer.com
HOW CAN I GET INFECTED WITH ICE VIRUS?
ICE Cyber Crimes Center virus, just like Your computer has been blocked virus, is distributed via trojan horse. Mostly, users download this infection together with unofficial programs and their updates that are spread on illegal websites. Besides, misleading emails that also pretend to be sent by this official organization can easily let this trojan inside. Once it gets there, this dangerous threat blocks the whole system and downloads those files that are needed for ICE virus. SO, it can be said that ransomware takes its target PC a hostage and then replaces desktop's screen with a message that claims something like that:
An ounce of prevention
At a bare minimal, always maintain a backup copy of any important files on your computer. Infection with this virus could require a complete wipe of the system and reinstallation of software to the factory settings. Depending on the number of apps on your system, this could be a labor intensive process that could cost an easy $200 for a technician to restore the system.As a preventative measure, we suggest having an IMAGE of your system made, using one of Richmond Computer's imaging tools.The image is made by our software, and would be stored on a series of DVDs or external USB drive.
For a consultation on the state of your system's backup, please contact Richmond Computer at (215)634-2997 or sales@richmondcomputer.com
Wednesday, January 22, 2014
Although this threat has been in existence for some time, we thought it would be educational for iPhone and Android users to be aware of this security hole on these devices:
Spyware takes over iPhones, Androids
31 August 2012
Call it Invasion of the iPhone Snatchers: a new FinFisher-based spyware is built to infect iPhones and iPads (and Android, BlackBerry and Windows Phone gadgets too) in order to take over the device completely – all unbeknownst to the user.
The smartphones and tablets will innocently appear to be themselves, but in reality the mobile malware is working in the background to track the device’s location, monitor activity and intercept communications including emails, voice calls and text messages.
Ironically, the malware was likely developed with the intention of aiding law enforcement. Citizen’s Lab at the University of Toronto has found that the functionality and mechanisms dovetail with Gamma Group UK’s product for tracking mobile devices.
“When FinSpy Mobile is installed on a mobile phone it can be remotely controlled and monitored no matter where in the world the target is located,” reads the product information. However, officials at the company have confirmed that a demonstration copy of its software has been stolen. Citizen’s Lab suspects that it is now spreading, in slightly altered form, at the hands of more nefarious elements.
The virus propagates itself via text message and email, prompting a user to download a bogus “system update” or click on an infecting link.
http://www.infosecurity-magazine.com/view/27909/spyware-takes-over-iphones-androids/
The smartphones and tablets will innocently appear to be themselves, but in reality the mobile malware is working in the background to track the device’s location, monitor activity and intercept communications including emails, voice calls and text messages.
Ironically, the malware was likely developed with the intention of aiding law enforcement. Citizen’s Lab at the University of Toronto has found that the functionality and mechanisms dovetail with Gamma Group UK’s product for tracking mobile devices.
“When FinSpy Mobile is installed on a mobile phone it can be remotely controlled and monitored no matter where in the world the target is located,” reads the product information. However, officials at the company have confirmed that a demonstration copy of its software has been stolen. Citizen’s Lab suspects that it is now spreading, in slightly altered form, at the hands of more nefarious elements.
The virus propagates itself via text message and email, prompting a user to download a bogus “system update” or click on an infecting link.
http://www.infosecurity-magazine.com/view/27909/spyware-takes-over-iphones-androids/
Tuesday, January 14, 2014
Microsoft Windows 9 by April 2015?
We know by now that Microsoft is terrible at meeting deadlines, however a tentative release date of April 2015 is now out on the internet for the release of the next version of Windows. The codename for the new version is Threshold.If Microsoft holds to its operating system pattern, Windows 9 will likely be an improvement and repair of all that went wrong with Windows 8, which to date, remains a shunned and disliked product. Microsoft hit it big in 1995 with Windows 95 and Windows NT. Three years later came Windows 98, which saw enhancements and improvements to '95. By 2000, Microsoft had released Windows ME, which was largely a marketing ploy of Windows 98 in a new skin. On the corporate side, Windows 2000 was a huge success. 2000 was the last release of Windows with a corporate and home use version that were on separate platforms.
Around 2002, Microsoft released Windows XP, which to date remains on some 30% of corporate workstations, despite Microsoft's insistence that all support for the product will end this April. XP was succeeded by Windows Vista, which was a very temperamental product that was shunned by end users. Most IT professionals, including us here at Richmond Computer, instinctively cringe when presented with a Vista based machine to work on.
Windows 7 succeeded Vista, and remains a popular and stable product, which is largely viewed as the matured version of Windows XP, with many added features, refinements and enhancements that never worked well in Vista.
Then came along Windows 8 and Microsoft's world stopped spinning. The geniuses in Redmond, Washington felt it urgent to consolidate user interfaces to present users with a single user experience. In short, the interface on your desktop would become the same as on your tablet, as the same on your Windows phone (which nobody buys).
The result with Windows 8 is that those who had to buy new machines bought them from sources that still sold Windows 7, or bought their own licenses and performed a self-install of Windows 7 over 8. Two important points here: While the interface in Windows 8 leaves much to be desired, and the "start button" enhancement that Microsoft added did nothing to fix what users said they didn't like, it is a stable platform, and the interface is similar to that of Server 2012.
While not much has been made public on how Windows 9 will address the failures of 8, we in the IT community trust that Microsoft has learned yet another lesson and will deploy a better product that is easier to use.
Wednesday, January 8, 2014
Gov. Chris Christie's Technology Bridge
As reported by the media, it has been discovered that New Jersey Governor Chris Christie's staff was involved in lane closures on a ramp that feeds the George Washington Bridge as political retribution. This situation came to light when the Asbury Free Press obtained emails and text messages from the Governor's office, we presume through the use of New Jersey's open records act/right to know law.
While we won't get into the political mess on this issue, there are two points that are important to note in our experience with electronic communications and investigations/court cases.
When parties enter litigation, evidence can be presented to prove a crime was committed or not committed, or to make a point when seeking damages under civil litigation. This evidence includes electronic communications, and those records can be sought under court order by opposing parties. That means if someone drags you into court, and they have a reason to believe you have email or text message records that prove their case, they can request a judge to order you to produce them. And if you deleted them, a reasonable effort must be made to recover them.
(aside: Richmond Computer specializes in recovering deleted text messages from iPhones and Androids)
While its fairly easy today for any of us to print emails or extract text messages for printing, producing only relevant parts of the conversation enhances the records by presenting as evidence only the parts of the communications that are needed to make the point/case. In addition, enhancements such as key word indexes give the requester or party presenting the information the ability to quickly identify relevant sections of the records needed in the investigation or court case.
One of the enhancements we add to our text message transcripts is page and line numbers, which allows litigants to quickly refer to specific communications during trial. In addition, we add in breaks to identify when conversations start and stop which add insight to how conversations unfolded.
View our transcript samples here:
http://www.richmondcomputer.com/doc/Transcript_2col_ColorBubble.pdf
http://www.richmondcomputer.com/doc/Transcript_ImStyle.pdf
http://www.richmondcomputer.com/doc/Transcript_UTF.pdf
While the rest of the world will be watching the future of Governor Christie's political career unfold, if you find yourself in need of an e-mail or SMS text message transcript, please contact us for a free consultation. We are based in Philadelphia, but our services are available nationwide.
http://www.richmondcomputer.com/text-message-transcripts.html
Keywords: Governor Chris Christie, George Washington Bridge traffic study, text message communications, text message transcript
While we won't get into the political mess on this issue, there are two points that are important to note in our experience with electronic communications and investigations/court cases.
1. Electronic communications are always discoverable
By discoverable, we don't mean these types of records can be found if you look in enough drawers. What discoverable means is depends on the situation: a) litigation or b) as part of an open records/FOIA request.When parties enter litigation, evidence can be presented to prove a crime was committed or not committed, or to make a point when seeking damages under civil litigation. This evidence includes electronic communications, and those records can be sought under court order by opposing parties. That means if someone drags you into court, and they have a reason to believe you have email or text message records that prove their case, they can request a judge to order you to produce them. And if you deleted them, a reasonable effort must be made to recover them.
(aside: Richmond Computer specializes in recovering deleted text messages from iPhones and Androids)
2. Presentation of electronic communications is key
As noted with the records obtained by NorthJersey.com, the email and text message records were not given any type of special formatting, enhancement or redaction (removal of personal/irrelevant sections of the record) when presented to the public.While its fairly easy today for any of us to print emails or extract text messages for printing, producing only relevant parts of the conversation enhances the records by presenting as evidence only the parts of the communications that are needed to make the point/case. In addition, enhancements such as key word indexes give the requester or party presenting the information the ability to quickly identify relevant sections of the records needed in the investigation or court case.
One of the enhancements we add to our text message transcripts is page and line numbers, which allows litigants to quickly refer to specific communications during trial. In addition, we add in breaks to identify when conversations start and stop which add insight to how conversations unfolded.
View our transcript samples here:
http://www.richmondcomputer.com/doc/Transcript_2col_ColorBubble.pdf
http://www.richmondcomputer.com/doc/Transcript_ImStyle.pdf
http://www.richmondcomputer.com/doc/Transcript_UTF.pdf
While the rest of the world will be watching the future of Governor Christie's political career unfold, if you find yourself in need of an e-mail or SMS text message transcript, please contact us for a free consultation. We are based in Philadelphia, but our services are available nationwide.
http://www.richmondcomputer.com/text-message-transcripts.html
Keywords: Governor Chris Christie, George Washington Bridge traffic study, text message communications, text message transcript
Saturday, January 4, 2014
Microsoft "One" - Has Microsoft lost their vision?
Microsoft was founded as a software company in the late 1980s as a development company focused on operating systems and productivity platforms. They hit gold in 1995 with Windows 95 and the subsequent releases of Microsoft Office.
By the late 1990s, Microsoft had carved out two successful niches to their market: business and consumer.
The consumer platforms consisted of Windows 95/98/XP Home Edition, whose trend continues through Windows 8.1 Home.
 |
| Microsoft's Redmond Campus |
The business platform grew exponentially into a number of platforms focused on the complex demands of business with data processing and storage. Some of the sucessful platforms included:
- Windows NT Workstation/Server
- The Windows Server platform
- Microsoft Exchange
- Microsoft SQL Server
- Microsoft Virtual Server/Hyper-V
In 2012, Microsoft began deployment of the new Office 365, which is a subscription based form of Microsoft Office. Instead of paying anywhere between $150 and $350 for a single license to use Word, Excel or Outlook, users now pay a fixed monthly fee. Microsoft expanded this to include the popular Microsoft Exchange service, which was traditionally hosted in house on a server. Servers running Exchange as a stand alone system often cost between $4,000-$8,000. One solution Microsoft used to offer was the small business platform. However, the final release of this product in 2010 was problematic due to instability caused by the way the system allocated memory. Microsoft's solution was to discontinue Small Business Server (SBS), calling it outdated with the gaining popularity of subscription based computing.
These changes may be fine, but with the release of Windows 8, Microsoft is now attempting to funnel business and consumer users into the same interface and platform with the new and difficult to use interface. Since mostly all business computer users also use computers for personal use outside of work, the rationale is to tie all platforms and devices together.
To further complicate Microsoft's vision, they now seek to be a purveyor of both software/services and hardware. One example is the Microsoft Surface tablet. Their survival strategy is to be in both devices and software for consumers and businesses, and to do that effectively, everything must be on the same page.
Microsoft is also seeking to keep everything under one roof, rather than split different divisions off into other companies. Remember the antitrust suits during the late 1990's?
At present, there is no need to "go Microsoft" to use Microsoft. Both Android and Apple platforms have been totally inclusive of Microsoft's hosted services. What is known is that Microsoft remains the stable platform for running real business apps such as Access (yes, people still use Microsoft Access) and integrating with domain based networks.
2014 Technology Trends - Devices and Services
There are many articles that speculate on what we can expect in terms of change and new capability in terms of technology for 2014. This post will attempt to quickly summarize and provide links to a sampling of these articles.
First, let's break down the trends into 2 categories: hardware and services. Software is not being included because at this stage of the game, most of the new capabilities are being delivered as a service, not as an "old fashioned" app that will be local to your device of choice.
First, let's break down the trends into 2 categories: hardware and services. Software is not being included because at this stage of the game, most of the new capabilities are being delivered as a service, not as an "old fashioned" app that will be local to your device of choice.
Hardware
Tablets: will continue to evolve in 2014. Samsung and other manufacturers now have tablets that rival Apple's iPad, which was once king of the tablet world. For example, the new Galaxy S3 tablet offers a more intuitive keypad verses the iPad's, which is sometimes clumsy when switching between letters and numbers. Most tablets today are cross platform compatible with email services and support the popular Microsoft Exchange service, which many today use as a service from service providers such as Richmond Computer, or Office365.
Desktop PCs: will continue to become scarce in households, but will rule the roost in the office. Windows 7 remains the preferred platform in the business place, but that could change as the cost of touch screen enabled systems comes down. Until then, efficient and cost effective will remain the dominant factor in choosing technology in most workplaces.
Services
Cloud based technology will continue to grow. We all use it now with email accounts, and many already use it for data storage, such as DropBox or Apple's iCloud. A few of our customers migrated to cloud based data storage and shed in-house servers in 2013. We expect that trend to continue as the replacement cycle for servers hits more customers in 2014.
Cloud based can be extended to activities as well. For example, distance learning via online courses continues to gain popularity at colleges. The cloud is becoming an experience through events such as online meetups where many users can interact at a single session. This replaces the once terse text based chatroom which was popular in the 1990s when pioneered by America Online.
Wearable Technology: Expect to see more of this as time marches on. In fact, a company has already developed a prototype edible technology comprised of a pill that is ingested and gives off a signal used for an individual to authenticate themselves to devices they touch: cell phones, doors, and even cars. This neatly solves the problem of having to remember complex passwords. Smart watches is another device attempting to permeate themselves into the marketplace.
Mobile Networks will continue to grow. As the amount of data we process continues to grow, so will the need to have bigger and faster networks.
Subscribe to:
Posts (Atom)





.jpg)
.jpg)
.jpg)